How cloud technologies change the production environment: a research
Contents
1. Cloud monitoring market 2020
The public cloud services market share in the global hosting industry was valued at $228 billion in 2019 and grew to $266.5 billion in 2020, an increase by 17%. Surely, the COVID-19 pandemic forced many companies to begin working remotely and move all IT operations they could to the cloud — yet some business-critical data must remain on-prem. Therefore, building hybrid cloud solutions is the obvious choice, and leading cloud vendors offer the tools to manage and monitor such environments using the latest technological advances.
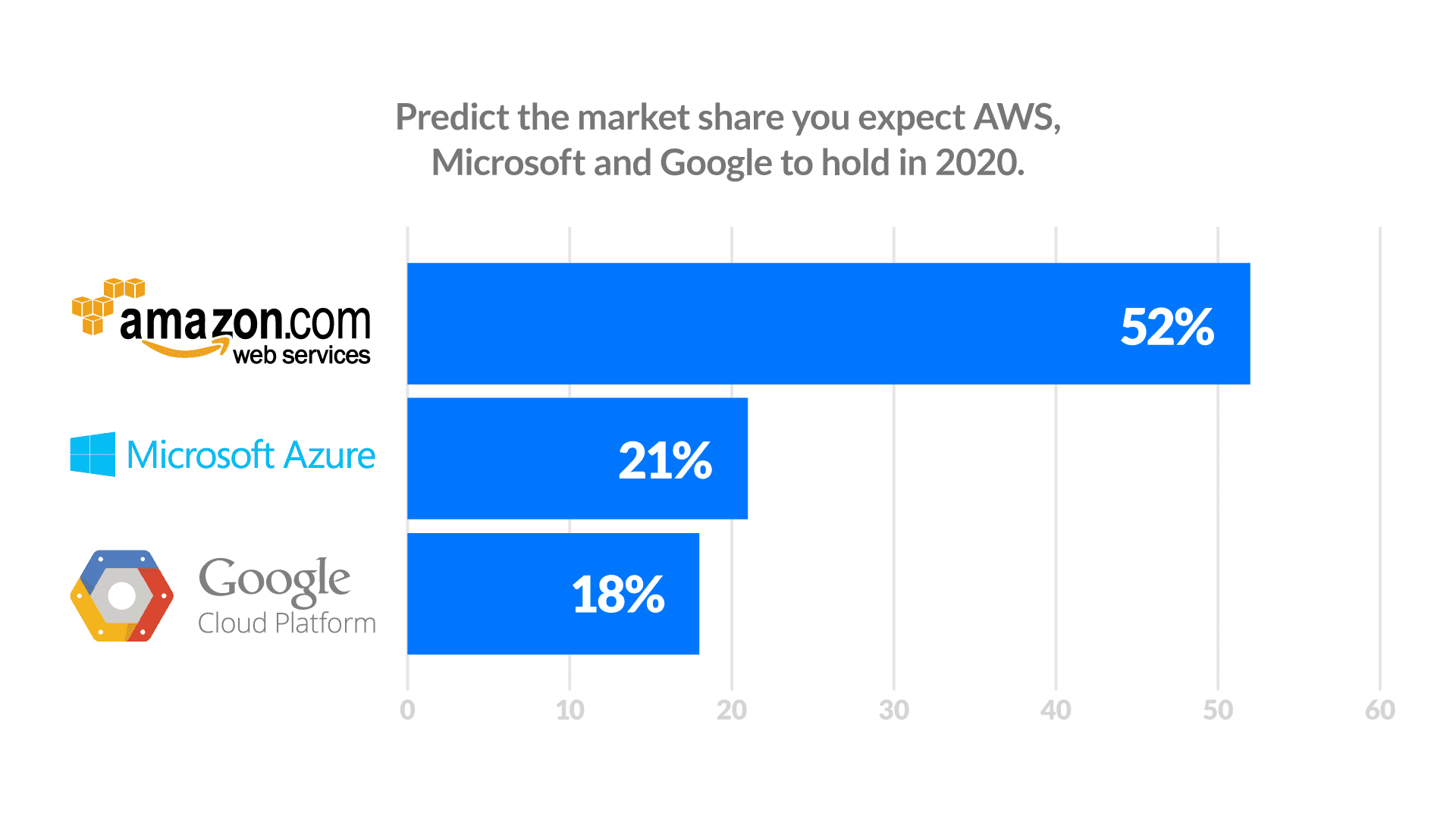
For example, Oracle cloud customer service now provides a cloud monitoring service leveraging AI/ML tools to monitor both traditional on-prem (Microsoft, Oracle) and public cloud (AWS, GCP, Azure) ecosystems. Scalability and operational flexibility are the key reasons why enterprise businesses shift their workloads to public, private or hybrid cloud environments. However, monitoring the performance of these highly-dynamic systems can be quite challenging without the correct set of tools.
Thus, the growing adoption of public cloud across various industries boosts the growth of the cloud monitoring tools market. Selecting the solution that meets your business needs best is an essential step towards transparent and efficient monitoring of your cloud infrastructure performance, resource allocation and spending.
As enterprises move their CRM, ERP, HRM and financial systems to hybrid cloud environments, they need to adopt new monitoring toolset to gain a holistic view of cloud performance metrics, customer flow, logs, data analytics and more.
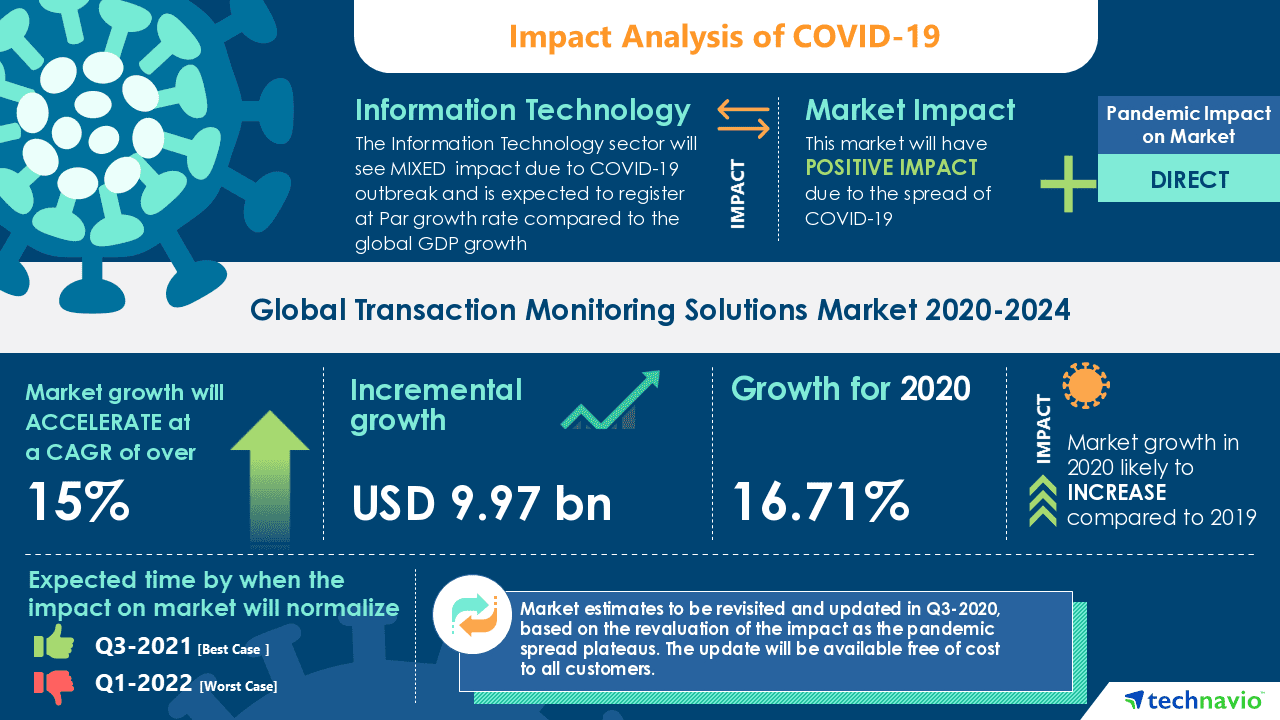
Nevertheless, implementing such systems requires quite significant investments, and selecting the wrong tool might provide insufficient visibility into the infrastructure performance which impedes widespread adoption.
2. Risks & Challenges in Cloud solutions
Cloud computing customers actually have quite limited visibility into the infrastructure performance side of things, unless they consume cloud resources under the IaaS model. However, when cloud computing resources are provided under the PaaS model, the customers cannot even monitor the hypervisor level. The need to control the performance of on-prem hardware in hybrid systems is another challenge.
Challenges of cloud solutions
A range of tools is required to adequately cover the performance of enterprise-grade hybrid cloud environments. The necessity to run multiple tools might hinder the adoption of such systems, as none of them f]provide the full scope of necessary features. Besides, connections to public cloud resources pose a cybersecurity threat to on-prem environments, increasing the potential attack surface. Thus, high costs and high level of expertise required to run hybrid cloud monitoring solutions slow down the growth of this market.
Top threats in the cloud: Data Theft, Cryptomining and Ransomware
IBM X-Force team IRIS conducted an in-depth analysis of cloud-related cybersecurity incident response cases they handled over the past 5 years. This allowed them to highlight the most widespread threats in the cloud and the trends of their evolution:
- Cybercriminals. Acting for financial gain cybercriminals are the most common and dangerous threat to any enterprise-grade cloud environment, though nation-state entities also pose a significant and persistent risk.
- Cloud app exploits. Cloud apps are the most common entry point into the systems. Hackers use methods like brute forcing, exploiting configuration drift and other security vulnerabilities to gain access to corporate systems. This is especially important with the “shadow IT” situation, when employees use cloud apps outside of the range approved by the company (like viewing Instagram or Tinder) on shift. As cloud app vulnerabilities were left outside the scope of traditional CVE’s till 2020, businesses have trouble handling them now, during the COVID-19 pandemic.
- Ransomware. Ransomware is the most widespread type of infestation in cloud environments, followed by botnets and crypto mining algorithms.
- Data theft. When hackers gain access to enterprise data, they steal all they can — financial data, personally identifiable information of clients and partners, emails, etc.
- External resources. Many malicious actors added cloud capabilities to amplify their DDoS or crypto mining attacks or just hosted the malicious software there to obfuscate their actions.
Charles DeBeck from IBM X-Force IRIS stated: “Malware cases targeting the cloud environments will grow in numbers, based on the trends we uncovered. Many malware developers are already adding disables for common cloud security features and write their malicious code in such a way as to leverage the scalability and agility of the cloud”
Focal points of hybrid cloud security
Massive shift towards remote work due to COVID-19 limitations makes online connections increasingly crucial for business operations. IBM security listed the following focal points for organizations using multi-cloud or hybrid cloud environments:
- Establish a unified cybersecurity governance. Adopt a holistic cybersecurity strategy and culture covering on-prem, cloud and security operations for Developers, IT Ops and Security. Designate clear roles and responsibilities for handling the existing and acquiring new cloud resources.
- Manage the risks. Perform risk-based assessment of the data, processes and digital assets you plan to manage in the cloud, create a roadmap for cloud adoption and instate appropriate security policies.
- Execute access management. Instate and uphold strict access management policies, including strong passwords and multi-factor authentication to exclude the possibility of system infiltration with stolen credentials. Execute zero trust model — impose restrictions on privileged accounts and provide the absolute minimum of necessary rights to all user groups.
- Use the right tools. Use open-standard security and monitoring tools to provide maximum interoperability and coverage for your on-prem and cloud environments.
- Train proactively. Hire forensic experts to provide simulated attacks. This will help highlight any potential security breaches and remediate them proactively. Rehearsing such attacks will help prepare response attack scenarios and tain your team, so they are ready when the real attack comes.
- Implement security automation. Effective automation of incident response scenarios helps greatly improve your detection and remediation capabilities, as compared to manual monitoring.
3. Why is it important to monitor usage and spending?
Cloud computing works under the Pay-as-you-go billing model, so you pay only for the resources you actually consumed. However, it is quite possible that some of your cloud instances are underutilized, so you will still end up paying for idling environments. Thus, monitoring tools like Cloudyn provide a cloud services dashboard that highlights the performance and utilization of your hybrid cloud computing resources, from virtual machines to cloud instances. This is essential to minimize spending, as exceeding agreement thresholds can cost quite a lot in the cloud.
4. Automated Monitoring for your business
There are several key benefits of using automated monitoring with Cloudyn as compared to manual ad-hoc monitoring and remediation.
- In-detail control. With manual monitoring, estimating costs based on average usage assumes the resource consumption is stable over time, which is rarely the case. On the contrary, using automated monitoring dashboards offered by Cloudyn helps quickly identify normal resource consumption trends and any deviations from them.
- Forecasts. Identifying resource usage trends helps make informed forecasts on their changes, thus allowing data-based planning of expenses.
- Alerting and notifications. Knowing your normal operational workloads allows setting thresholds and preparing response scenarios based on notifications. These help handle the resource consumption fluctuations. Moreover, you can have alerts to inform you of a sudden resource usage spike due to a DDoS attack. etc.
Automated monitoring means reduced operational overhead and financial expenses.
5. What Is Cloudyn for business?
Cloudyn is a subsidiary of Microsoft with features similar to Azure Cost Management (ACM). It provides in-detail dashboard reports on cloud resources allocation, usage and monitoring for Azure, AWS, GCP and other cloud service providers.
Cloudyn dashboards are customizable widgets that provide a high level view of your systems. This makes Cloudyn a single platform for enabling in-detail monitoring and resource management for public, private and hybrid cloud environments. Since acquisition by Microsoft in 2017, Cloudyn has enabled in-depth monitoring cost management for Azure< GCP, AWS and other enterprise cloud systems. This helped greatly reduce the cost-efficiency of cloud transition and ongoing usage for multiple Microsoft customers.
While initially providing only Amazon API integration, Cloudyn soon acquired customers who used multiple clouds, including AWS and OpenStack. They needed visibility into their multi-cloud ecosystems, but more importantly, they needed a clear overview and a piece of advice regarding their budget allocation across several cloud platforms.
In cooperation with the Cloudyn development team, AcademySmart solved this challenge in 6 months! Read the full case here: https://academysmart.com/portfolio/.
6. How to use Cloudyn to manage costs?
Let’s briefly describe the cost management process with Cloudyn.
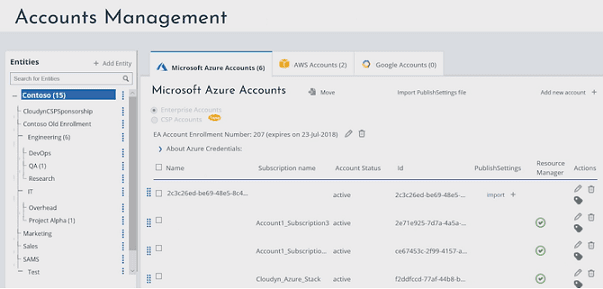
- Cloudyn projected costs reports use historical data as a basis for forecasts of resource allocation and costs.
- All accounts, entities and resources can be tagged to ease grouping and filtering.
- Subscriptions can be added to various cost entities.
- Actual Costs Analysis aggregates all the data over some interval to provide visibility into how and where your resources are spent.
- Sizing Optimization and Inefficiency reports can be used to make your data usage more efficient and thus, reduce costs.
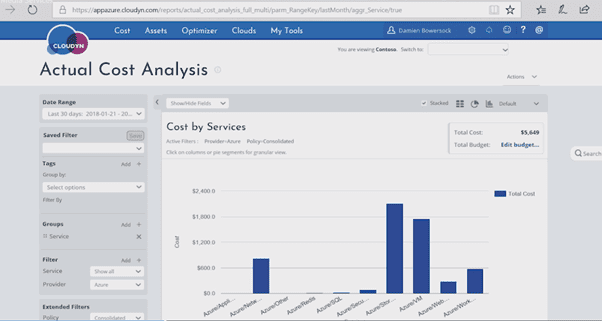
7. Reports and reporting features Cloudyn
Cloudyn provides three main types of reports: Over Time, Analysis and Tabular.
- Over Time reports show the time series data over a selected interval. Detailed filtering and grouping help concentrate on points of interest and enable tracking of overall trends, anomalies and resource consumption spikes.
- Analysis reports aggregate data for certain periods. They also provide filtering and grouping to showcase root causes of the anomalies.
- Tabular While all reports are available as tables, reports like Recommendations can only be viewed in tabular form.
Any type of report can be delivered on demand or according to schedule. Furthermore, you can use the Costs report to set a threshold and alert on your resource consumption.
Reports and reporting features
- The Cost Analysis report can be used to aggregate the data on your cloud resource consumption over a selected time period based on your cost allocation policies and tag categories.
- The Cost Over Time report provides a time series view on your cost allocation and helps provide visibility into any normal spending patterns, anomalies in resource consumption and cost spikes.
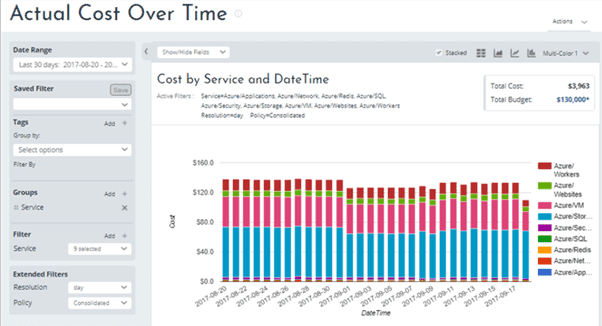
- The Actual Cost Over Time report provides filtering and grouping, and highlights cost allocation over a specified time interval to identify trends, anomalies, and spikes,
For example, the image below shows filtered services on an Actual Cost Over Time report.
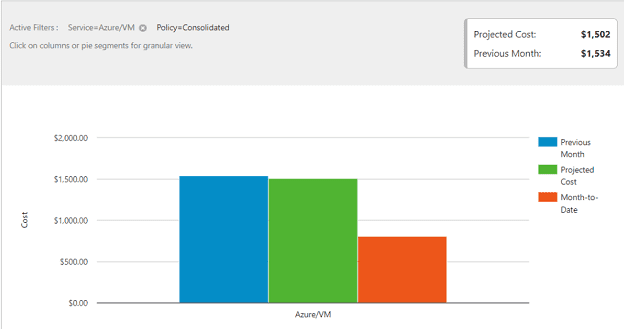
- The Current Month Projected Cost report provides data on the previous month costs, month-to-date costs and the projected total cost for this month by service or by account.
- The Annual Projected Cost report uses a trend function to extrapolate the projected costs for the next 12 months based on previous spending trends.
- Optimizer reports are useful to identify underused Virtual Machines and avoid moving them to the cloud. This helps optimize your infrastructure and reduce costs when moving from on-prem virtualization to the cloud..
- The Cost-Effective Sizing Recommendations report helps identify the possible annual savings by comparing VM instance type capacity to their historical CPU and memory usage data.
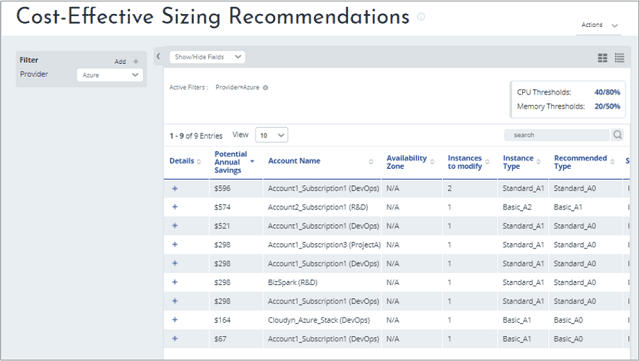
8. Forecast Period Cloud Technologies
Global market of cloud monitoring platforms is forecast to grow at a CAGR of nearly 20% during the next 5 years. The ever-present need for cost-effective resource consumption monitoring and security is the most powerful market growth driver. In order to increase the speed and agility of their operations, the end-user industries are massively adopting cloud computing, which further boosts the pace of market growth.
Selecting the right cost management and resource consumption tool is essential for ensuring your business leverages public, private, hybrid or multi-cloud environments with utmost cost-efficiency. Contact us if you have any further inquiries or want to create a cloud monitoring solution to fit the unique operational DNA of your business!
Book a free consultation

Reach out to start talking today!